Remove the Fog of Unknown Cloud Applications
As a technology professional, security has always been at the forefront of my thought process. I’ve been interested in security since I started in the industry in 2007. Back then, security was  present, but much less complex than it is today. Most companies had the majority of their IP and other resources locked in an internal network with technologies like NTFS, on-premises applications and team sites in SharePoint.
present, but much less complex than it is today. Most companies had the majority of their IP and other resources locked in an internal network with technologies like NTFS, on-premises applications and team sites in SharePoint.
Thanks to the iPhone’s release in 2007, data accessibility took the business world by storm. Everyone either had one or was getting one. The ease of use opened up new opportunities and ways to work. The world as we knew it was connecting like we could never have imagined just a few years earlier. Laptops were being phased in as the choice of workstation and VPN’s were being opened to all employees. Work from home schedules began to be a perk a company would offer to attract top talent.
With this proliferation of remote and ubiquitous data access, corporate IT security was quickly getting a lot more complex.
Today, everyone has a smartphone and can access data from anywhere. They do this through both IT sanctioned and their own personal applications. This is because employee and employer expectations about how and when work gets done have shifted. As a business competing in today’s world, you can either get on board or get left behind.
This new way of working presents many challenges when it comes to IT security, but one of the biggest is what to do about the incredible amount of cloud applications and services that employees are using. There are thousands of applications out there that just require a credit card to get going (or worse, are free) and IT has no insight into what is happening.
This is Shadow IT at its finest. IT doesn’t move fast enough or an end user feels empowered and the next thing you know, your business’ data is out there, unmanaged.
There are thousands of cloud-based applications out there and so many places corporate data could end up, many IT organizations have just thrown their hands up and are hoping for the best. How can you corral your end users and get them using IT sanctioned apps, while weeding out the risky apps?
The first step to finding out what your employees are using isn’t as difficult as you think.
Microsoft’s Cloud App Security allows IT to get these answers and do something about it. By checking your network egress traffic and using analytics up in Azure, you can easily identify which cloud-based applications your employees are using.
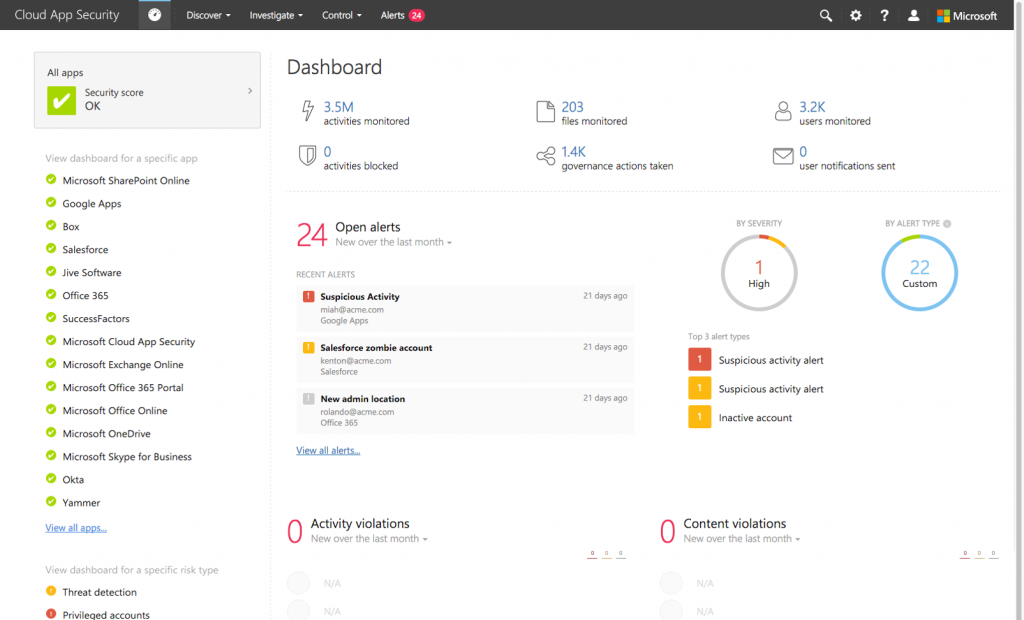
Microsoft takes this a step beyond simple identification though. By layering on intelligence about specific cloud-based applications, you can assess your company’s risk instantly and build control around high-risk applications. For those you want to allow to manage and have APIs, you can set a policy and even gain certain insights into what employees are doing.
In order to maintain corporate IT security, you know exactly what applications your employees are using and exactly how many. And with this information, your able to effectively sort through the fog that the cloud creates and take the steps necessary to protect your organization.
Celebrate Cybersecurity Awareness Month with Arraya
October is National Cybersecurity Awareness Month. All month long, Arraya’s award-winning Microsoft team members will celebrate by sharing their insights into some of the latest security solutions from Microsoft and how these tools – along with a partnership with Arraya – can help businesses reach their cybersecurity goals.
Visit www.arrayasolutions.com/contact-us/ to open up a dialogue on cybersecurity (or any other IT topic) with a member of our team. We can also be reached by emailing mssales@arrayasolutions.com or through social media: Twitter, LinkedIn, or Facebook.
