How to Better Secure Your Cisco Expressway

Given the current pandemic situation, the remote work culture has become our new normal. Companies that previously considered Work from Home (WFH) a perk, offered only to certain individuals, have had to open it up to a wide range of employees. Aside from the obvious upsides, this poses a few security concerns as well. So, it is strongly recommended that companies keep up with regular security audits & follow accepted best practices. In this blog post, we’ll look at one such best practice and how to accomplish it.
Specifically, this applies to Cisco shops running VCS/Expressways at the collaboration edge. Best practice is to make sure you have upgraded your TLS Versions with highly secure Cipher suites.
Need help doing so? Don’t worry, you are in the right spot.
Starting with version X8.10, Expressway defaults to TLS Version 1.2 when establishing secure connections for the following services:
- HTTPS
- SIP
- XMPP
- UC server discovery
- Reverse proxy
However, on upgrade, the previous behavior and defaults persist so you won’t be defaulted to TLS version 1.2. New installations will use the new defaults. So, for new installations you should check that all browsers and other equipment/applications that must connect to the Expressway supports TLS version 1.2.
Cipher Suites:
You can configure the cipher suite and minimum supported TLS version for each service on the Expressway. These services and cipher suites are shown in the table below. (The cipher strings are in OpenSSL format.)
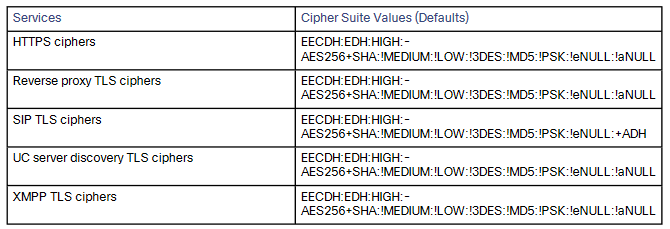
For services where the Expressway can act as a client, for example HTTPS, the same minimum TLS version and Cipher suites will be negotiated.
Configuration:
- Login to the Expressway(s) with admin credentials.
- Go to Maintenance > Security > Ciphers.
- Configure the minimum TLS versions & supported Cipher Suites (refer table above) as required.
- Save & restart the Expressway(s) for the changes to take effect.
- Note that these changes must be completed in both C & E expressways.
- In a clustered environment, the changes can be completed only in the primary configuration node & it propagates to all the cluster nodes.
Here is a video reference: https://video.cisco.com/video/5858449075001.
If you need any help with the above steps, don’t hesitate to reach out to the Arraya team! We’ll be happy to share our insights and expertise. Do so by visiting: https://www.arrayasolutions.com//contact-us/!
