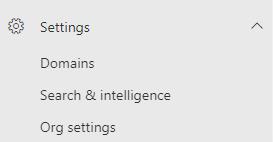
Already bracing for a potentially long winter due to spiking COVID-19 cases, those in the healthcare industry could soon be forced to fight a battle on a different front. Last month, a trio of government agencies warned of “an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” This comes as multiple institutions have already reported falling victim to what one expert described as “the most significant cybersecurity threat we’ve ever seen in the United States.”
At the end of October – which is coincidentally Cyber Security Awareness Month – the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) – issued Alert AA20-302A “Ransomware Activity Targeting the Healthcare and Public Sector.” This alert warned of an ongoing campaign leveraging malware-boosting platforms like TrickBot and BazarLoader as well as ransomware strands like Ryuk for profit, data theft, and service disruption. Included within the alert were technical deep dives into the malicious technologies at play as well as indicators of compromise.
Reporting by NBC News suggests more than 60 separate healthcare ransomware infections so far this year in the US, up from 50 in 2019. And those are just the incidents that have been made public. Given the usual lag that exists between the onset of an incident and its disclosure, it’s likely that number is far higher. So far, those attacks have forced doctors and nurses to resort to paper and pen record-keeping and even necessitated the re-routing of ambulances. While far from ideal, these complications also don’t fit the bill of a true worst-case scenario. Germany experienced exactly that kind of tragic outcome earlier this year when a ransomware attack left a hospital’s systems offline, resulting in the death of a person seeking emergency care.
Ransomware best practices for IT and users
Even under the best of circumstances, an attack on a healthcare facility could leave lives hanging in the balance. Now, as providers fight to beat back the steadily rising tide of COVID-19 cases nationwide, it’s clear why an expert dubbed one of the groups allegedly behind these campaigns as “one of most brazen, heartless and disruptive threat actors I’ve observed over my career.” While it may seem like a tremendous task given the scarcity of resources and mental bandwidth within most facilities right now, it is possible to stay digitally safe during these incredibly trying times.
Here’s how IT admins and end users can both help stop ransomware, informed by the government’s AA20-302A alert and our team’s own in-the-field experiences.
IT admins should:
- apply patches throughout their technology environment, preferably as soon as they’re released from manufacturers. If IT is continually underwater with patch releases, look into shifting that responsibility over to a managed services provider.
- practice proper password hygiene for admin accounts, including choosing unique, complex passwords and activating multifactor authentication where available.
- scan the network for open ports, taking care to disable any that remain open but are going unused. Still-active ports should be closely monitored to vet the authenticity of traffic.
- partner with users to identify critical digital assets, including patient data and telehealth/work infrastructure and create the necessary redundancies to keep those assets available even in a worst case scenario. This should include performing regular backups, apply air-gapping between production and backup files, and securing with password/encryption.
- audit all account access privileges, particularly those granted admin rights, with an eye toward reducing access to the lowest level necessary for the account to still function.
- implement network segmentation, to keep valuable data points separate from each other and to make it harder for attackers to move freely throughout an environment should they gain an initial foothold.
- deploy intelligent automation where possible to speed up malware detection and mitigation efforts, also minimizing the error risk often associated with manual processes.
- never agree to pay a ransom and do whatever is necessary to avoid ending up in a situation where that seems to be the best, or only, option. Paying a ransom encourages future attacks and doesn’t guarantee access to data will be restored (See: Last year’s NotPetya attacks).
As for users, they should:
- know how to spot red flags indicating a phishing email, a frequent first step in ransomware campaigns, including:
- unexpected requests for sensitive or high-value information (ex., credentials, financial details, etc.).
- persistent typos or awkward phrasing. No one is immune to the occasional typo. However, emails that would wear out spelling and grammar checks might indicate the person on the other end isn’t who they claim to be.
- email addresses that, at first glance, appear legitimate but upon closer inspection are shown to only be close approximations of an authentic account (ex., replacing an uppercase I with a lower case L).
- links that, when hovered over, are revealed to direct the recipient to somewhere other than where the text of the message claims.
- feel empowered to confirm requests for credentials or financial information with leadership using alternate channels (IM, phone, etc.) rather than by responding directly via a potentially compromised email thread.
- participate in regular training to better understand the methods cyber criminals will use to try to compromise them.
- understand where to turn if they feel a message they received might be malicious.
- feel comfortable reporting any interactions with a potentially malicious message or link right away, giving IT valuable time to react.
Next Steps: Living out your ransomware worst case scenario (sort of)
The most basic thing every organization needs to have in order to survive a ransomware attack is a plan. Every level and department needs to understand that, if something goes wrong, they should respond by doing X,Y and Z. This plan should lay out in detail how technical teams, organizational leadership, those on the operational side, PR teams, etc. should respond. However, having a plan isn’t enough. Every potential tripping point or question should be smoothed over and answered before that plan is put into practice.
Need a hand building out or stress-testing your incident response plan? The Arraya Cyber Team (ACT) can help. Our experts can work with you to build out and then step through a fictional disaster scenario. Such exercises are completely customizable and can cover everything from attempts to repel attacks to what would happen should hackers actually get inside your network. This latter point may be uncomfortable to think about, but is too important to overlook. Reach out to ACT to learn more about our Tabletop Incident Response Workshops or to schedule yours now!
Visit https://www.arrayasolutions.com//contact-us/ to connect with our team now.
Comment on this and all of our posts on: LinkedIn, Twitter, and Facebook.
Follow us to stay up to date on our industry insights and unique IT learning opportunities.