Microsoft Inspire kicked off on July 18th with CEO Satya Nadella’s keynote, providing information on a plethora of AI-centric products including Microsoft Copilot, Bing Chat Enterprise, and Llama 2 by Meta. He was joined by other executive members who addressed key partnerships at Microsoft and enhancements in Microsoft’s Partner Program that would allow partners to deliver AI-ready solutions and services to their customers.
In this post, we are going to provide further details on the Inspire announcements that we’re most excited about and how Arraya Solutions plans to help deliver these products and services to customers like you!
Bing Chat Enterprise
Bing Chat Enterprise is Microsoft’s solution to providing businesses with an AI tool that is secure, private, and free from data leakage. By leveraging Microsoft’s AI principles, Bing Chat Enterprise will provide your users with the power of Bing Chat but with secure principles in mind.
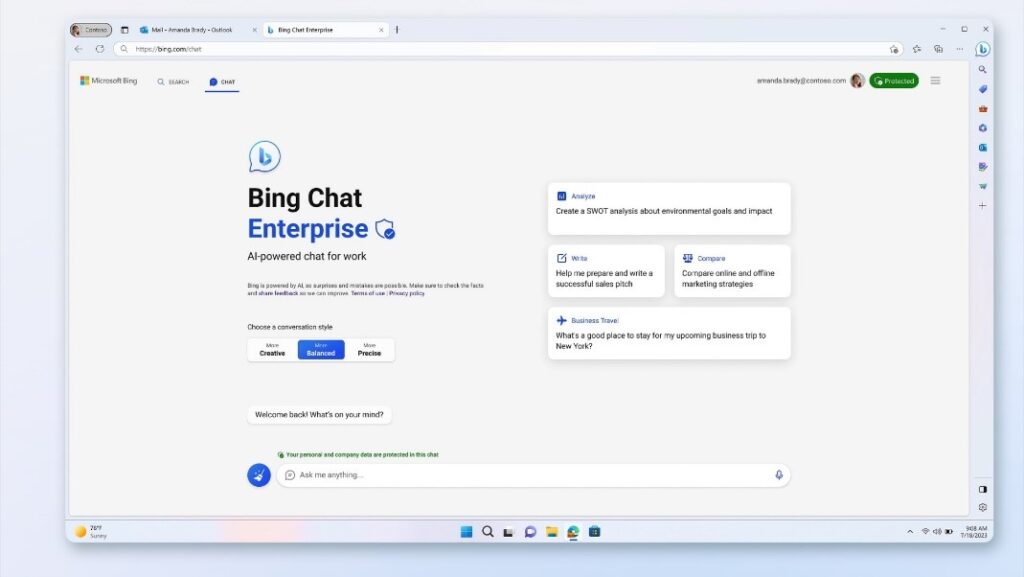
Data cannot be accessed by Microsoft, chat history is never recorded, and data provided is not used to train the model. You can rest assured that by supplying proprietary data for analysis, summarization, or key phrase extraction, this data will be protected and enhance your everyday workflow.
Bing Chat Enterprise is available today at no additional cost for Microsoft 365 E3, E5, Business Standard, and Business Premium subscribers. If you are not subscribed to these products, Bing Chat Enterprise can be purchased at a standalone offering of $5 USD per user per month.
Microsoft 365 Copilot & Sales Copilot
Microsoft 365 Copilot, one of Microsoft’s most anticipated products, was announced earlier this year. Copilot is built with enterprise-grade security, privacy, identity, compliance, and responsible AI. This means that Copilot will inherit your existing security, privacy, identity, and compliance policy, ensure data is logically isolated to your tenant, and respect the user and group permission policies.
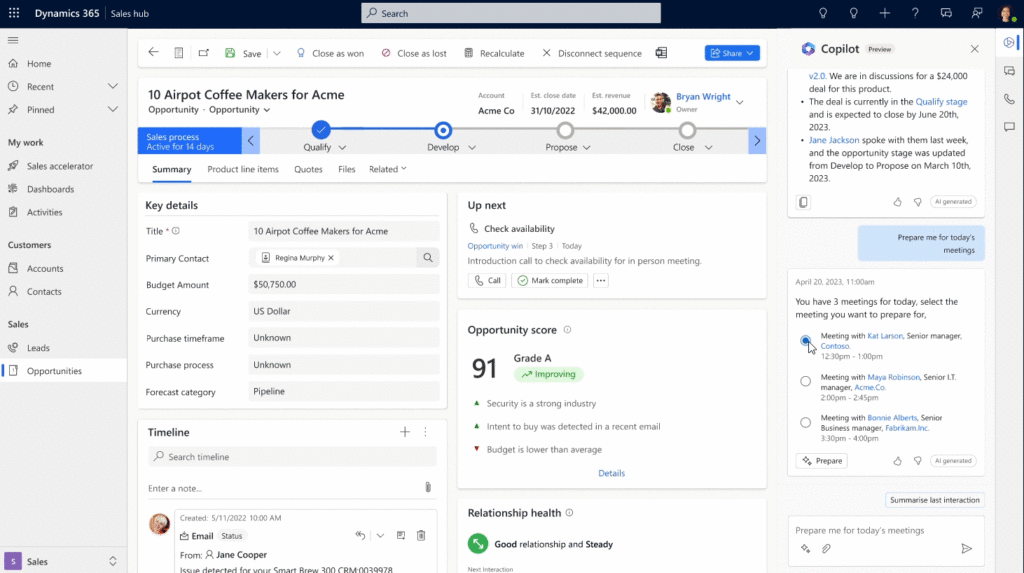
Copilot will be available in all Microsoft productivity products including Outlook, Teams, Viva, and Office apps such as Word, Excel, and PowerPoint.
During this year’s Inspire, Microsoft provided information on Copilot pricing as well as Microsoft Sales Copilot which empowers sellers to increase productivity and personalize every customer interaction. Built into CRM related programs like Dynamics 365, Outlook, Teams, or even Salesforce, Sales Copilot will enable your sellers to do what they do best!
Microsoft CoPilot will be available for commercial customers for $30 USD per user per month for Microsoft 365 E3, E5, Business Standard, and Business Premium customers.
Azure Capabilities & Investments
As you and your business rationalize your workloads to determine if they are cloud ready, Azure has received some new enhancements which can bolster your estate as you migrate to the cloud. Enhancements such as Extended Security Updates (ESU) for Windows Server 2012/R2 systems hosted in Azure or enabled by Azure Arc, enhanced assessment tools in Azure Migrate, Llama 2 integration to Azure AI, and GitHub Advanced Security for DevOps.
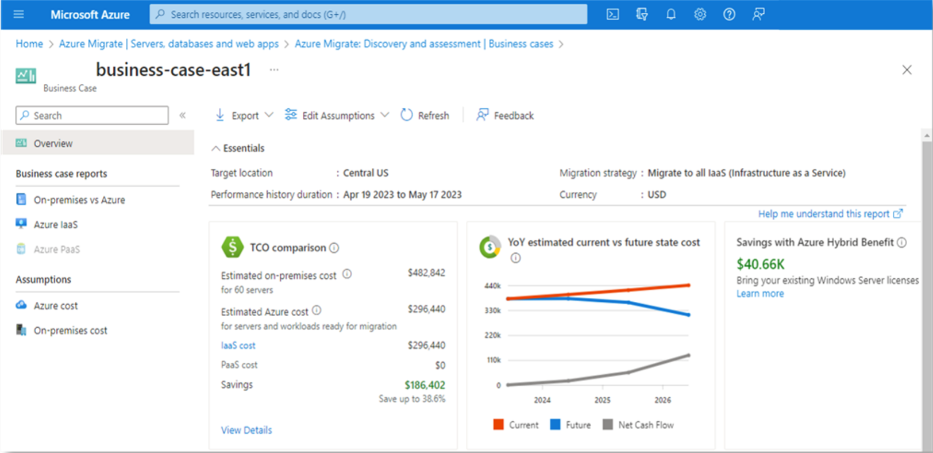
We’ll touch base on a couple of these.
Upgrading your Windows Server 2012/R2 systems to 2016 and higher can be a difficult task if they host mission critical workloads. That is why, come October 2023, Microsoft is offering their customers the ability to install extended security updates to ensure your workloads remain protected.
To achieve this, you can purchase ESU subscriptions from Partners like Arraya or enable your workloads with Azure Arc and use technologies, such as Update Management, to push those updates to your systems. Additionally, Azure Migrate now supports in-place upgrades of Windows Server 2012/R2 servers to later operating systems (OS). If you cannot upgrade the OS, bring the OS as is and it will receive free extended security updates.
Lastly, Microsoft has partnered with Tanium, a 2023 Microsoft Partner of the Year, to help enhance your workload assessments with real-time operational data that can be used by Azure Migrate to build a business case without the need of installing an Azure Migrate appliance on premises.
Next Steps: Take Advantage of the Latest in Cloud Computing
Arraya’s chosen top releases are just the tip of the iceberg on what new Microsoft products can do for your organization. Today, Arraya is dedicated to helping you with assessing your current state to determine if you’re ready for implementing the cloud fully or in a hybrid way.
Reach out to one of our account executives today to schedule a consultation!
Visit https://www.arrayasolutions.com//contact-us/ to connect with our team now.
Comment on this and all of our posts on: LinkedIn, Twitter and Facebook.
Follow us to stay up to date on our industry insights and unique IT learning opportunities.









