Since the tail end of last year, our Data Center team has been helping us unpack the hype surrounding VMC on AWS. So far,  through three blog posts, we’ve covered how this partnership simplifies data center migrations, introduces new layers of security through NSX microsegmentation, and alleviates some common disaster recovery pain points. The final topic our team wants to explore as part of this series concerns VMC on AWS tools native to the solutions and how they contribute to the hype surrounding it and the value it can provide.
through three blog posts, we’ve covered how this partnership simplifies data center migrations, introduces new layers of security through NSX microsegmentation, and alleviates some common disaster recovery pain points. The final topic our team wants to explore as part of this series concerns VMC on AWS tools native to the solutions and how they contribute to the hype surrounding it and the value it can provide.
The catalog of AWS native tools is nothing short of daunting. Diving into every unique application and its associated use cases would require its own blog series. Instead, our team decided to focus on three tools that, from their perspective, generate the most positive industry buzz.
Each of the following VMC on AWS tools is available to those using VMware and Amazon’s cloud service. After we look into each one, our team will also preview a feature on its way to VMC on AWS. This upcoming feature could soon join the ranks of the most talked about and leveraged.
Amazon Relational Database Service (RDS)
Managing organizational databases is a time and resource-intensive job. Staying on top of security, monitoring performance, backup – all of these tasks (and more) can eat up much of an admin’s workday. The longer that admin is tied up with necessary, but routine, maintenance tasks, the less time he or she has for projects that push the business forward.
Amazon RDS through VMC on AWS provides a database as-a-service experience, allowing organizations to free database admins by automating the time-consuming tasks above. RDS can also automate failover, minimizing downtime in the event of a worst-case scenario.
When it’s time for an application to scale, RDS can help there too. It can provide the room apps need to scale, requiring little more than a few clicks to provision the necessary compute or storage assets. RDS also works across the most popular database engines on the market, including SQL Server, Oracle, MySQL, and more. This ensures operational continuity as organizations can continue using the tools with which they’re most familiar.
Amazon Simple Storage Service (S3)
For many modern organizations, complexity has become a defining characteristic of the data center. Skyrocketing demands surrounding capacity, durability, etc. have pushed some to pursue best-of-breed solutions to those problems. However, a piecemeal approach can result in environments that are increasingly difficult for IT pros to manage and secure.
The name of Amazon’s Simple Storage Service (S3) feature says it all. This Amazon native tool can deliver vast, easily scalable quantities of reliable object-based storage to VMC on AWS shops. Organizations can relocate as much as they choose into S3, paying only for the space they use. That data can be anything, including backups, IoT-generated analytics and beyond, all with a guaranteed durability of eleven 9s (99.999999999%).
Also, S3 enables unmatched, granular data control. Admins can manage their data at either the account, bucket, or object level. It doesn’t matter if they’re replicating, auditing, or performing some other management task. They can do so across any level.
Elastic vSAN
The last presently available feature our Data Center team wanted to highlight is also one of the most recent additions to the VMC on AWS tool chest. The hardware upon which customers’ VMC on AWS deployments are built comes with a fixed amount of useable block storage. However, among adopters there was a growing demand for more storage space and more compute power to go along with it.
Enter Elastic vSAN. This tool combines Amazon’s Elastic Block Store with VMware’s vSAN storage solution. Organizations can use this feature to expand their available storage capacity using Amazon’s own native block storage.
Furthermore, Elastic vSAN is able to reduce downtime in the event of a problem through its auto-remediation feature. If an issue affects a given host, a replacement will become available and automatically incorporated to ensure service continuity.
Coming Soon: VMC on AWS Outposts
Finally, VMC on AWS Outposts is a new tool set to arrive during the second half of 2019. For a variety of reasons, not all data is able to reside in the public cloud. VMC on AWS Outposts intends to bring a SDDC infrastructure as-a-service experience to these otherwise grounded data sets.
As part of VMC on AWS Outposts, organizations will gain access to software-defined services covering compute, storage, security, and more. This solution will be able to run VMs, containers, and Kubernetes-based apps in the hybrid cloud, one based inside either a customer’s own data center or at a designated co-lo facility.
Next Steps: Further your VMC on AWS knowledge and skills
Want to learn more about VMC on AWS tools or the solution as a whole? You can reach out to our Data Center team at any time by heading to https://www.arrayasolutions.com//contact-us/.
VMC on AWS will also be one of the featured topics at the 5th Annual Arraya Tech Summit. This by techs, for techs event features a full day of deep dives into the topics and trends impacting today’s IT professional. The session, VMC on AWS and What It Might Mean for the Present (& Future) of the Data Center, will focus extensively on VMC on AWS as the true hybrid cloud solution. Attendees will gain a greater understanding of VMC on AWS’s role in the evolution of the data center, particularly as it pertains to disaster recovery, hybrid integration, and cyber security.
The Arraya Tech Summit will take place on June 6th at the Sheraton Valley Forge in King of Prussia, PA. To learn more or reserve your spot, visit: https://events.arrayasolutions.com/.
 this year, we published a blog post citing Gartner research projecting
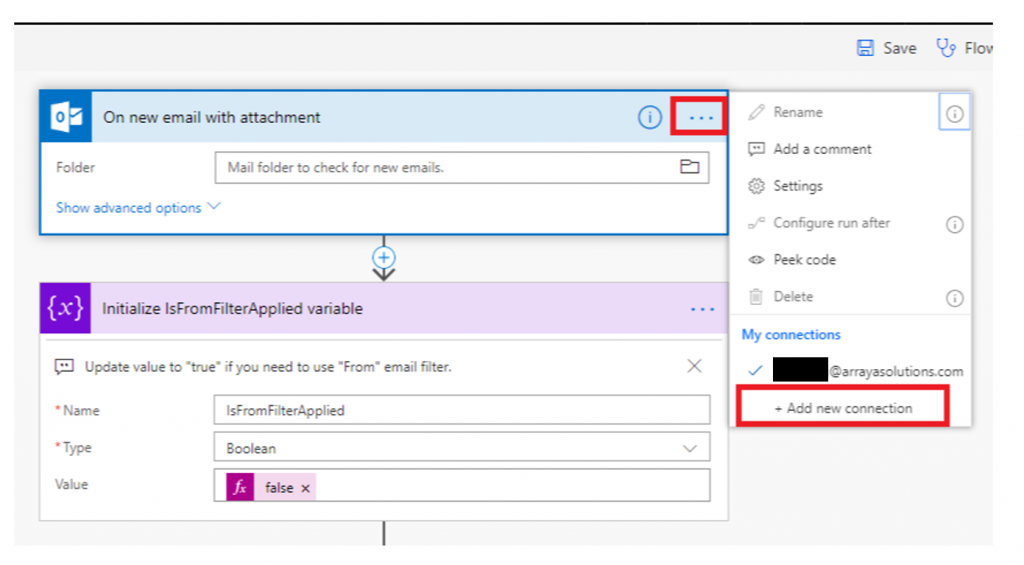
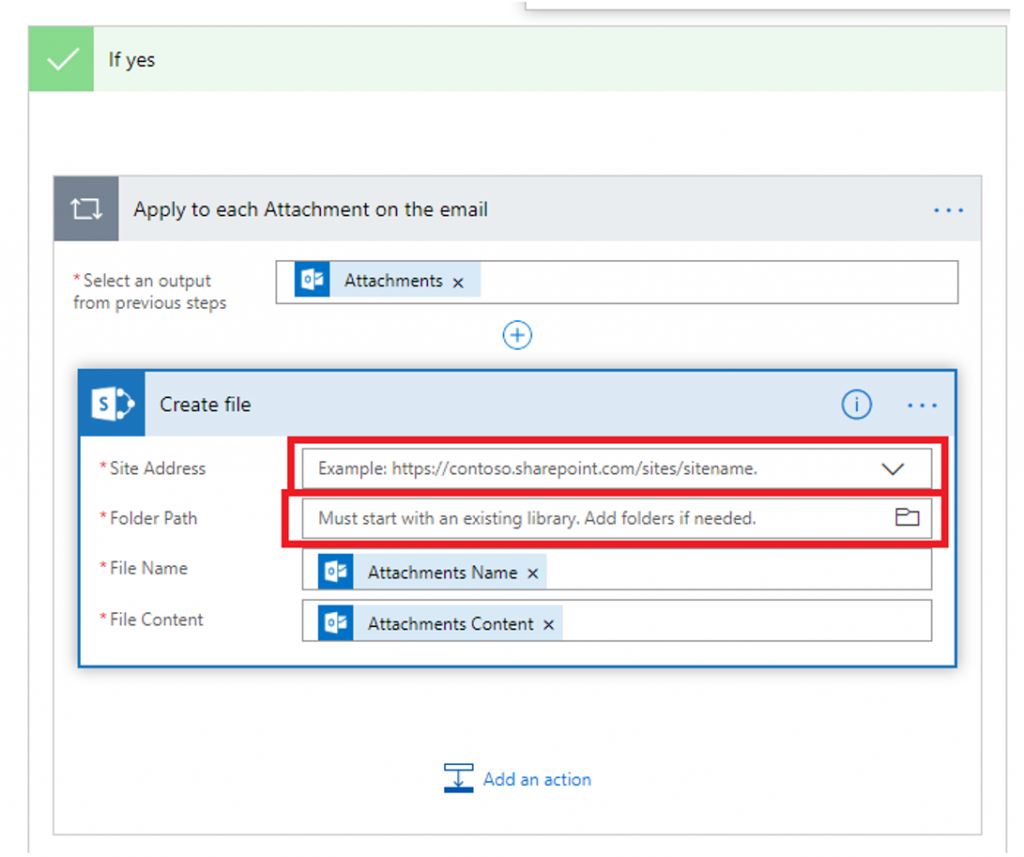
this year, we published a blog post citing Gartner research projecting  appear to exist at all. The latter is true of one of SharePoint on-prem’s more-popular capabilities: incoming email. While this time and headache-saving ability doesn’t exist in SharePoint Online yet, you can spin up an approximation of it. Even better, doing so doesn’t require a deep understanding of and devotion to all things SharePoint.
appear to exist at all. The latter is true of one of SharePoint on-prem’s more-popular capabilities: incoming email. While this time and headache-saving ability doesn’t exist in SharePoint Online yet, you can spin up an approximation of it. Even better, doing so doesn’t require a deep understanding of and devotion to all things SharePoint.
 and levels of an organization together quite like being annoyed by meetings. In that way, they’ve become something of a great corporate unifier. While it’s unlikely Cisco’s cognitive collaboration effort will transform meetings into anyone’s favorite time of day, the tech giant has its sights on making them more productive and efficient – and less painful.
and levels of an organization together quite like being annoyed by meetings. In that way, they’ve become something of a great corporate unifier. While it’s unlikely Cisco’s cognitive collaboration effort will transform meetings into anyone’s favorite time of day, the tech giant has its sights on making them more productive and efficient – and less painful. worried. Data protection is becoming an existential issue. It’s hard to imagine any business feeling confident enough to call themselves challenge-free. It raises the question, are those organizations ready for anything, data protection-wise, or are they overestimating their capabilities? Is an unnoticed, unaddressed challenge waiting to do significant damage?
worried. Data protection is becoming an existential issue. It’s hard to imagine any business feeling confident enough to call themselves challenge-free. It raises the question, are those organizations ready for anything, data protection-wise, or are they overestimating their capabilities? Is an unnoticed, unaddressed challenge waiting to do significant damage? alone. A recent survey from Computer Weekly and TechTarget found just over half of IT pros (52%) see upgrading Windows
alone. A recent survey from Computer Weekly and TechTarget found just over half of IT pros (52%) see upgrading Windows  stories represent valuable learning opportunities for organizations seeking to avoid a similar fate. Let’s review each story, then we’ll share some insights into how companies can protect themselves.
stories represent valuable learning opportunities for organizations seeking to avoid a similar fate. Let’s review each story, then we’ll share some insights into how companies can protect themselves.