October is Cyber Security Awareness Month and after all this talk of awareness, it’s time to focus on action.
Even if you’ve been intentionally avoiding the bad news, it’s no secret that the cyber risks we face today are a problem for everyone. So now it’s time to break through the bad news bias and look to the positives. Yes, cyber risks are on the rise, but with a proactive security practice, your organization can significantly reduce its risk.
Cybersecurity is everyone’s problem. We can all take an active role in combating these threats and making cybercrime a less lucrative and enticing operation.
Here are 5 tactics to focus on now to start building a proactive security practice:
If you have to start somewhere in your security practice, this is the place. Today, MFA is essential. Any business looking to get a cyber insurance policy will likely find that MFA is one of the first of many prerequisites they’ll need to be considered.
Multi-Factor Authentication (MFA) and Privileged Access Management (PAM) provide a multi-layered defense to protect your business.
MFA is a security method in which two forms of credentials (or authentication) are required prior to being granted access to an account or system, rather than relying on a single password alone. PAM is a locally deployed software solution that is used to “secure, control, and monitor access to an organization’s critical information and resources.”
Together, MFA & PAM will allow you to monitor what users are doing, verify that users are truly who they say they are, and identify anything that deviates from the norm so your organization can respond quickly.
- Segmentation
Network segmentation is a security technique that divides a network into smaller, distinct sub-networks in which unique security controls can be applied. This technique allows security teams to administer more specific controls to portions of your network that require higher security.
Further, with segmentation, a malicious actor will only have access to the small portion of your network they infiltrated, rather than all of it. It can be expected that network segmentation will be a more common regulatory compliance requirement moving forward.
Micro-segmentation takes this a step further to provide highly granular visibility and control over data flows within your system.
- Secure Backups
A business is only as good as its last backup. With today’s cyber climate, a secure and reliable backup is a necessity for when the inevitable strikes, which means not all backups are created equal.
There are a number of questions your business can consider to harden your backups, including:
- Are you identifying and classifying your data?
The process of data tagging means identifying your data as public, private, and confidential. Employees should be trained in both how to tag data and how to properly classify it. When a breach occurs, it can be a waste of time and resources to recover all your data. With a data classification system, you can quickly identify what data is critical and necessary to continue business operations.
- Are you conducting recovery testing and validating your most critical data?
Critical data should be backed up more frequently. Regular recovery validation testing should be completed to ensure this data will be ready and available when it’s needed most.
- Should you consider backup immutability?
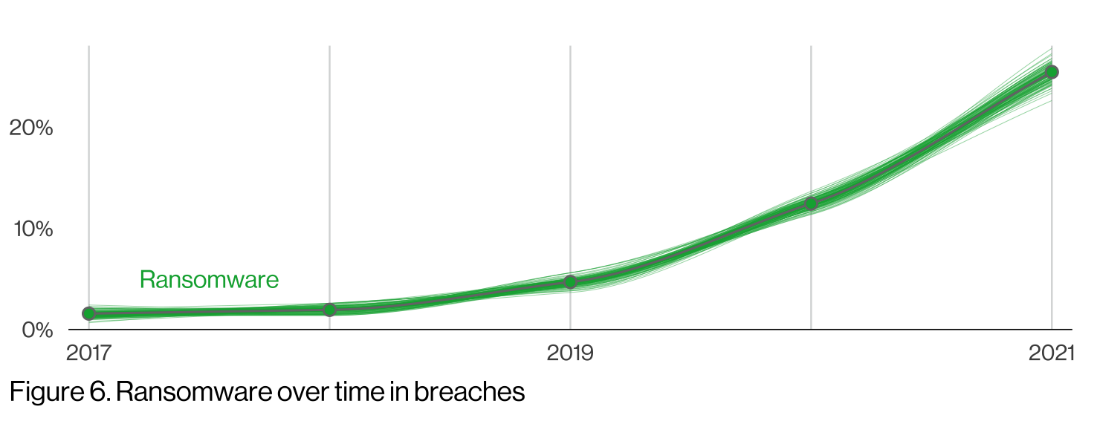
As the threat of ransomware grows, some malicious actors are targeting data backups first. Backup immutability provides copies of your data that cannot be altered, encrypted, or deleted which makes it much more difficult for ransomware attackers to make a ransom demand.
- Where do your backups live?
Backups stored offsite will take significantly longer to restore than backups housed within your network, however, they can also be more secure offsite. Each organization will have to weigh the pros and cons associated with the location options they have access to.
- What type of access controls do you have?
Ideally, every business would have both Network Access Controls (NAC) and Role-Based Access Controls (RBAC) implemented to reduce the risk of unauthorized devices, networks, and individuals reaching data backups.
- Assessments
Security assessments are a common requirement for regulatory compliance. However, these hold much more value than simply checking a mandatory box.
Conducting the right assessments in the appropriate order will provide useful insights in your organization’s security posture so you can identify vulnerabilities and address them before they’re exploited. There are several types of security assessments that provide different insights, depending on your needs:
- Business Impact Assessment
- Risk Assessment
- Penetration Test
- Tabletop Exercise
As these assessments represent a single point in time, they should be conducted regularly to check in, and see where your company stands.
- Endpoint Detection & Response
An endpoint detection and response (EDR) security solution detects threats across your environment and contains them within the endpoint so they can’t spread. This type of solution also investigates how the threat got in, where it’s been, what it did, and what to do about it now that it’s been identified.
Next Steps: How to Balance Security with End User Experience
It’s no secret that security methods and precautions can be a headache for end users. That extra step, like a second layer of authentication, can have a big impact on security but can also be a hassle to deal with on a regular basis.
Leadership should keep an open line of communication with end users on the controls being rolled out. It’s important to track the metrics of the efficacy of those security controls against the impact they’re having. What burdens are they putting on users? What is realistic and what isn’t?
Consistent training is key. This will keep employees up to date on the latest cyber threats and help them understand how these threats work, and why the security methods implemented are a necessity. Interactive training has proven to be the most effective in both areas.
It’s time to reflect on your organization’s security, and determine what’s working, what isn’t, and what can be changed to make your security position stronger than ever for next year.
To learn more about improving your security posture, contact one of our Arraya Cyber Team experts today.
Visit https://www.arrayasolutions.com//contact-us/ to connect with our team now.
Comment on this and all of our posts on: LinkedIn, Twitter and Facebook.
Follow us to stay up to date on our industry insights and unique IT learning opportunities.