By now we’ve all heard about ransomware and the massive financial implications it can have on business. While ransomware is an example of ![]() something coming in and infecting you, the converse can be a risk. With the ease of cloud accessed Software-as-a-Service (SaaS) applications, your data can be outside of IT’s control extremely easily. Two recent examples of disgruntled employees illustrate just how important IT’s management of SaaS applications can be.
something coming in and infecting you, the converse can be a risk. With the ease of cloud accessed Software-as-a-Service (SaaS) applications, your data can be outside of IT’s control extremely easily. Two recent examples of disgruntled employees illustrate just how important IT’s management of SaaS applications can be.
Recently, a for-profit college in the Midwest was held hostage by a newly-terminated employee. For some unfathomable reason, this single employee had just enough access to bring the school to its knees by locking it out of its access to a SaaS based education application. The employee made financial and job-related demands and claimed the school caused the service lockout, not malicious actions.
Regardless of who is at fault in this instance, for the school, the primary concern was for the services impacted and the real financial implications of being offline and locked out of its cloud application.
Direct financial implications and service loss are a couple of ways for individuals to impact a company. Another way is to attack the brand over social media – using the company’s own accounts! One infamous event had an employee tweeting from the company’s account to their 63,000 followers while in the middle of mass layoffs. This person still had the ability to take this action, even during their own termination, due to the lack of IT control. Given the number of cloud-based applications most employees use on a day to day basis, it is easy to see how some could slip through the cracks in IT.
There are two main issues that need to be covered in the scenarios above. The first issue is identifying and securing access to critical applications. The second is controlling access to those applications. Despite these two different instances, you can build a cohesive solution to address both with Microsoft.
Let’s start by finding out what cloud applications are in use. An easy way is with Cloud App Discovery, a component of Azure Active Directory Premium. This tool provides a way to discover what cloud-based SaaS applications are in use on your network, who is using them, and help prioritize which applications the IT department should begin managing. This method does require an agent, but offers much more in-depth information about what your users are doing with the SaaS apps.
To take discovery to the next level and layer on control, Microsoft offers Cloud App Security. This component of Enterprise Management + Security provides the tools necessary to both discover and manage cloud-based SaaS apps. With Cloud App Security, you can first discover which SaaS apps are in use on your network without deploying any client agents. Then, using the information gathered, you can determine which apps IT should be managing access to (and which ones you may want to block altogether). Cloud App Security allows IT to create policies around how different SaaS apps are used in the enterprise, including methods for Data Loss Prevention (DLP) for these apps.
Once you know which SaaS applications are in use, you need to control access to them. Azure Active Directory also includes a Single-Sign-On (SSO) component for most popular cloud apps. Using SSO, access to third-party apps is granted or terminated in a single effort, by configuring a user’s Active Directory account. In some cases, such as the Twitter example above, the end-user doesn’t even know the password to the corporate Twitter account. Once their Active Directory account is disabled (which should have happened as soon as that person entered the room) the user can no longer access Twitter. If they are the only one responsible for the account at the company, it is a simple process to add another user to the application, and the company maintains control of their social media. The same concepts apply to the college example, as well.
If these examples or the solutions discussed hit close to home for you, or have you wondering how SaaS applications are being managed in your organization, reach out to Arraya’s Microsoft team today to discuss our Enterprise Mobility + Security Pilot, which includes Azure Active Directory Premium SSO, at mssales@arrayasolutions.com.
They can also be reached through Arraya’s social media accounts: Twitter, LinkedIn, and Facebook.
 migration
migration  from turning that fantasy into reality?
from turning that fantasy into reality? that your business should squeeze itself into one of their service tiers, and they promise you won’t need anything else beyond that. They see standard service options as a path to efficiency. The more streamlined their offerings, the more predictable their operating costs will be (and the larger their profits over time). It’s neat and tidy, but in reality, how often can you say either of those things about life in IT?
that your business should squeeze itself into one of their service tiers, and they promise you won’t need anything else beyond that. They see standard service options as a path to efficiency. The more streamlined their offerings, the more predictable their operating costs will be (and the larger their profits over time). It’s neat and tidy, but in reality, how often can you say either of those things about life in IT? forgive the paraphrase of a popular horror movie trope – the tool that would allow you to do those things is already in your data center.
forgive the paraphrase of a popular horror movie trope – the tool that would allow you to do those things is already in your data center.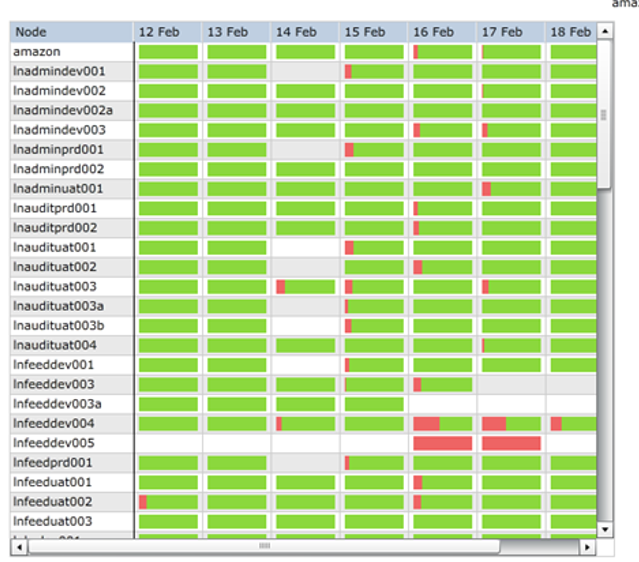

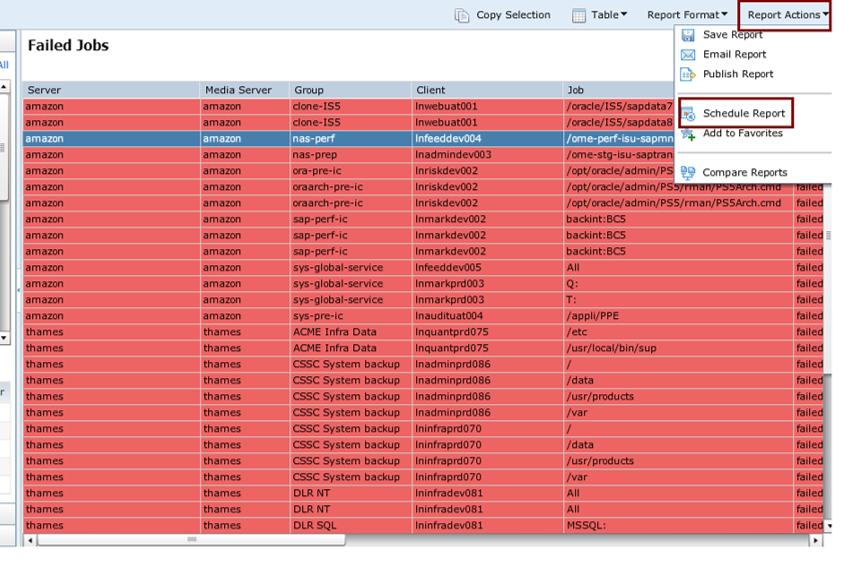
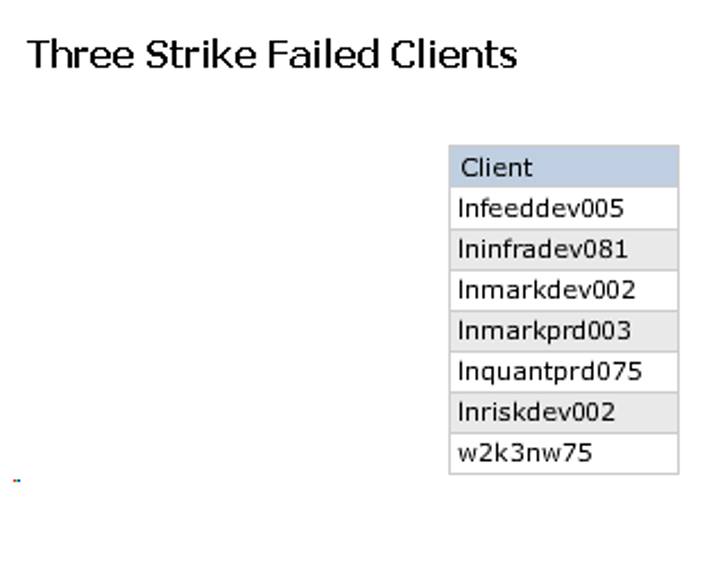
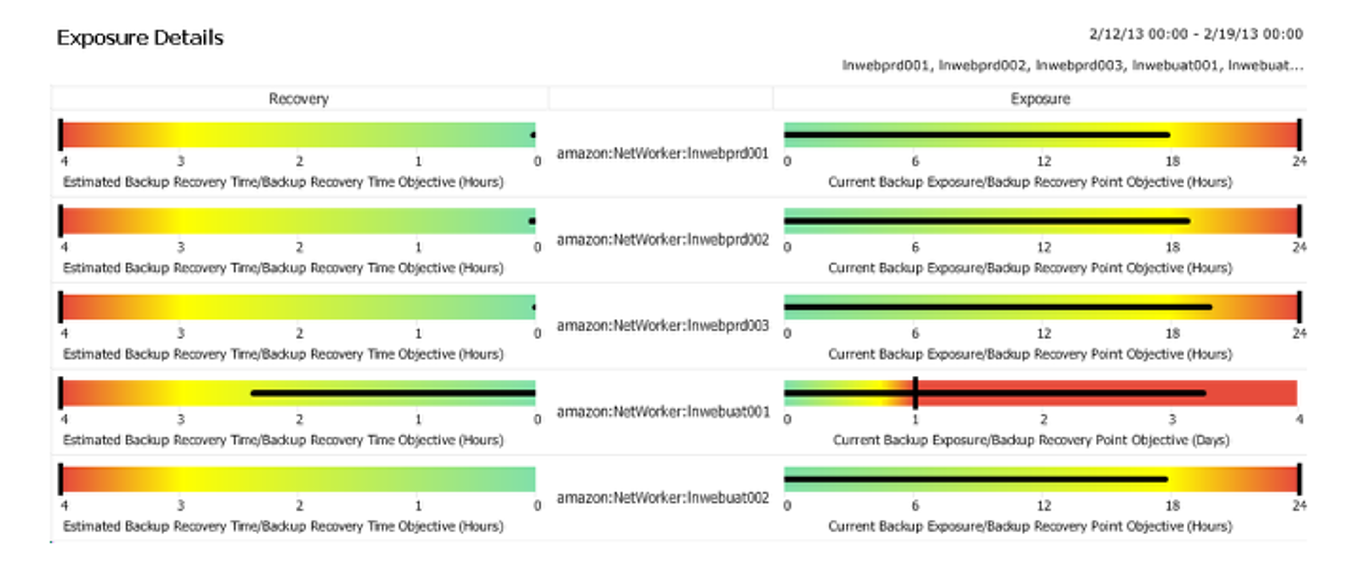
 costs. Some experts are estimating the security breaches will end up costing Yahoo around $1.5B. The Identity Theft Resource Center also recently released a report of confirmed data breaches for 2017. In total, they identify 144 breaches that exposed over 1 million personal records. The incidents they reference span across multiple industries and companies.
costs. Some experts are estimating the security breaches will end up costing Yahoo around $1.5B. The Identity Theft Resource Center also recently released a report of confirmed data breaches for 2017. In total, they identify 144 breaches that exposed over 1 million personal records. The incidents they reference span across multiple industries and companies. tightly integrated union of compute, storage, networking, and virtualization capabilities – will enter the “mainstream.” That prediction lines up with statements from Forrester concerning
tightly integrated union of compute, storage, networking, and virtualization capabilities – will enter the “mainstream.” That prediction lines up with statements from Forrester concerning  ng. This year’s report collects the insights of roughly 3,000 Chief Security Officers and security operations leaders from around the world. Surprisingly, amongst the talk of rapidly-evolving, high-tech threats,
ng. This year’s report collects the insights of roughly 3,000 Chief Security Officers and security operations leaders from around the world. Surprisingly, amongst the talk of rapidly-evolving, high-tech threats, 
 traditional signature based antivirus software will block 50% of the malware out there. What I’m saying is that, when used correctly, endpoint protection software can significantly reduce the likelihood of compromise. Typically antivirus software is installed in “set it and forget it” mode which is why it’s so ineffective. Listed below are 5 ways endpoint protection software is often misused and how to better utilize it:
traditional signature based antivirus software will block 50% of the malware out there. What I’m saying is that, when used correctly, endpoint protection software can significantly reduce the likelihood of compromise. Typically antivirus software is installed in “set it and forget it” mode which is why it’s so ineffective. Listed below are 5 ways endpoint protection software is often misused and how to better utilize it: