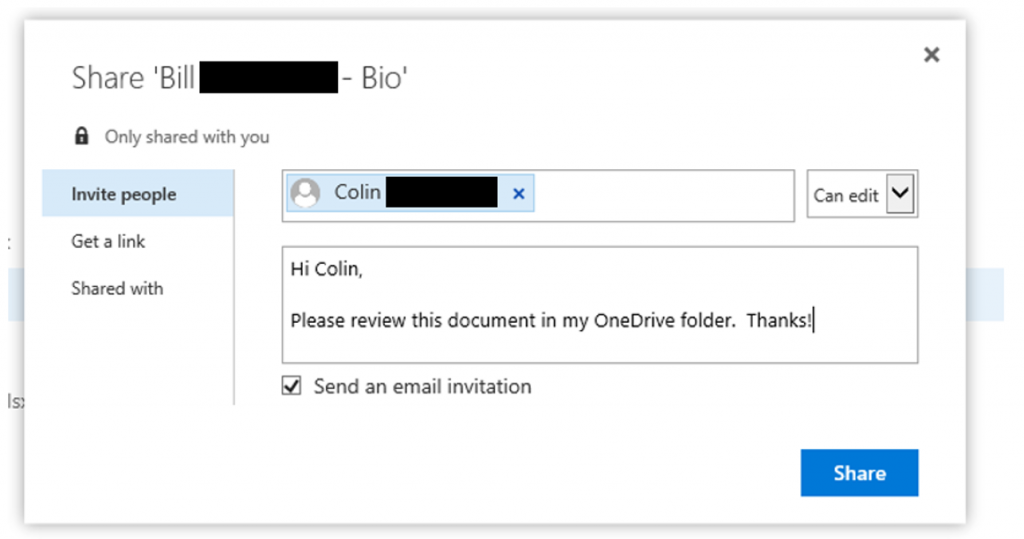
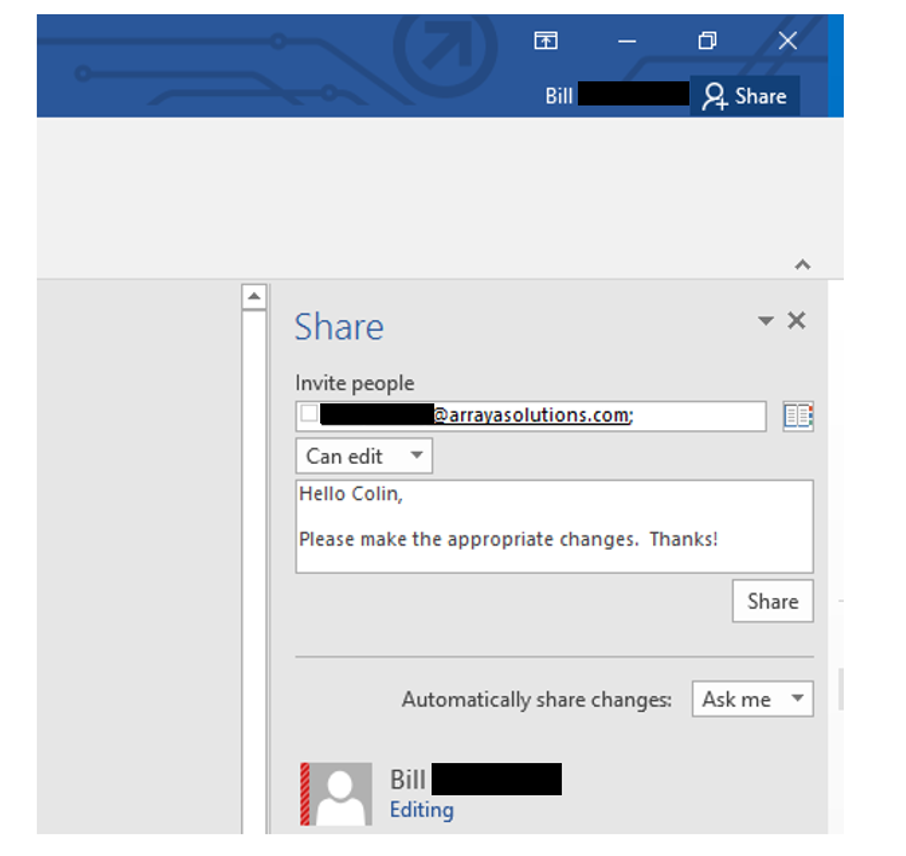
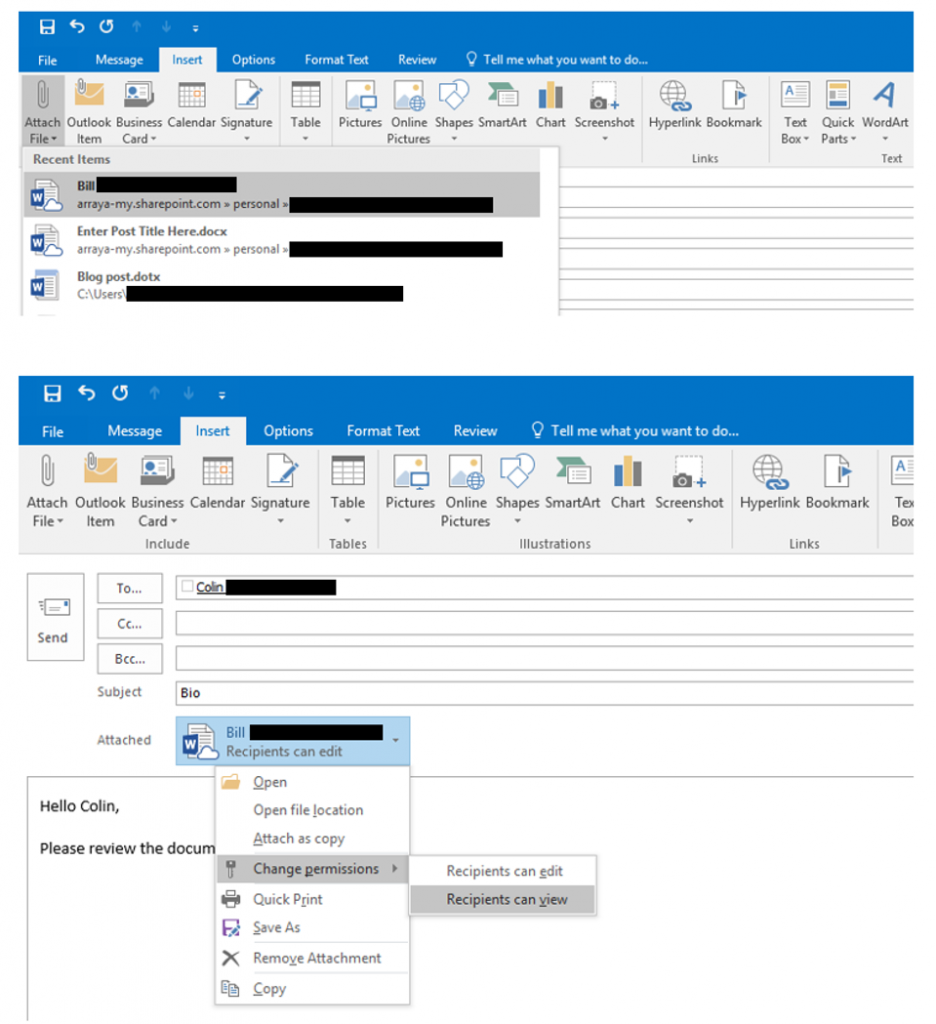
Employees are the best defense against costly ransomware attacks, according to one recent study. Of the organizations who participated, 89% listed employee awareness training as an effective way to protect themselves against ransomware threats. That was more than enough to claim the top spot on the best defense list, even putting it ahead of backing up files (83%).
an effective way to protect themselves against ransomware threats. That was more than enough to claim the top spot on the best defense list, even putting it ahead of backing up files (83%).
It makes sense. All it takes is one employee clicking on one shady email attachment and suddenly all your peers are reading about your company for all the wrong reasons. Logical as it may be to focus on employee training, there are a couple of issues with it.
One is timing. As IT’s workload grows, end user training is often one of the first things pushed to the back burner.
Beyond that, no matter how much training an employee goes through, there is still a chance he or she clicks on a dubious email attachment anyway. Maybe it came over before the employee’s morning coffee kicked in or maybe it came at the end of a long day. Either way, the result is the same.
Responding to a ransomware attack
Some have already dubbed 2016 “the year of ransomware.” It’s hard to argue considering the volume of headlines these types of attacks seems to generate. That label is unlikely to change, at least according to the same study mentioned above. Roughly 93% of respondents said ransomware incidents will increase during the remaining months of 2016.
Besides regular training and backups, what else can mitigate the risks posed by ransomware and other types of malware? One element missing from some ransomware response plans is a way to quickly detect and isolate ransomware once it enters the network. This is where network segmentation with a hand from Cisco TrustSec technology can help.
TrustSec is software-defined technology embedded in devices such as network switches, routers, etc. These devices are logically sorted into groups based on their role, their position, and so forth. They allow cybersecurity teams to add and alter network segmentation patterns based on grouping, eliminating the need to overhaul the network itself.
This solution perfectly complements several other Cisco security tools – including a pair that we’ve covered in this space before: Cisco ISE and Cisco FireSIGHT. Think of an organization’s TrustSec-powered devices as individual points on a page. ISE is the grid connecting those points. ISE lets you configure those points, build policies, and push configurations out to them. Watching over all of this – and really the entirety of a security architecture – is FireSIGHT. It gives security teams a centralized location from which to monitor and respond to policies and events.
Another piece of this puzzle is Cisco’s Advanced Malware Protection (AMP). Cisco’s global threat intelligence team monitors the latest developments in malware, pushing that information out to AMP, which can help adjust an organization’s defenses accordingly. AMP will also monitor the behavior of files that make it into the corporate network in search of anything suspicious.
All of that being said, here’s how a ransomware response would look with these solutions leading the charge:
- An end user opens a message and clicks on the malicious link contained within.
- AMP analyzes the file, and – if it’s a known threat – sends up a red flag. If it’s not a known threat, AMP continues to monitor the file until signs of trouble emerge.
- Once a red flag goes up, this information is delivered to ISE.
- ISE pushes out a quarantine policy to the affected area based on group designation, alerting the TrustSec-enabled devices to the problem.
- These devices are cut-off from accessing the rest of the corporate network, isolating the malware/ransomware and minimizing the damage it can inflict.
- The full scope of the incident can be analyzed using FireSIGHT during clean-up – a process that will be much less time-consuming than it would normally be in this situation.
A more-complete vision for malware defense
Healthcare, education, even government. It doesn’t matter what vertical you call home, ransomware and malware must be a top concern this year and in the years to come. Certainly training employees on where not to click and practicing proper back-up procedures have roles to play in preventing/minimizing risk.
Businesses must also be prepared to quickly and efficiently manage an infection should one happen. TrustSec technology, paired with ISE and FireSIGHT provides the foundation businesses need to deliver on that objective.
Want to learn more about TrustSec or any of the security solutions mentioned above? Have a question about network security in general? Reach out to our team of security experts by clicking HERE. They can also be reached via social media – Twitter, LinkedIn, and Facebook.

 achieving it is not. For today’s cyber crooks, data breaches are a business and, according to one recent survey, business is booming.
achieving it is not. For today’s cyber crooks, data breaches are a business and, according to one recent survey, business is booming. made a shocking return to the public eye. The storage devices featured prominently in a
made a shocking return to the public eye. The storage devices featured prominently in a  was booming and the traders pushed the technology envelope at the company. We were one of the first companies to adopt RIM’s Blackberry pagers (yes, I said pagers).
was booming and the traders pushed the technology envelope at the company. We were one of the first companies to adopt RIM’s Blackberry pagers (yes, I said pagers). and off their plates. Whatever the motivation, moving too quickly from the decision to pursue a project to starting it can spell trouble.
and off their plates. Whatever the motivation, moving too quickly from the decision to pursue a project to starting it can spell trouble.
 without, assigning the task to a project’s lead engineer or tacking those duties onto another employee’s workload. These businesses may view a dedicated PM as a luxury rather than a necessity – a misconception that could spell disaster.
without, assigning the task to a project’s lead engineer or tacking those duties onto another employee’s workload. These businesses may view a dedicated PM as a luxury rather than a necessity – a misconception that could spell disaster.