Last year, I can remember attending the pre-opening of the Microsoft Store in King of Prussia. They had the new Surface Books there and in stock. After trying the Surface Pen and seeing the improvements over my Surface Pro 3, I was sold.
The device has been rock solid. I detach the top and carry it around while I do presentations. I even watch Microsoft Mechanics videos on it while I’m on the treadmill. Yet, something has been plaguing my Surface Book lately and it finally came to a head this week.
A number of articles cropped up this week about the issue that I was seeing on my Surface Book, the dreaded “Sleep of Death.” The symptoms are this – you walk away from your Surface Book for even a few minutes, it goes to sleep and…never…wakes…up (cue scary music)! This resulted in a lot of lost productivity, even with the Office document recovery features.
I did a little bit of poking around and after 2 days, I can confidently say that this fix has worked for me. If you are tech savvy and plagued by the same issue, I encourage you to try this. As with any technical advice though, you should always make sure you have recent backups and are at a point where you can spend time troubleshooting your device if things go south.
This is a 2 step process. First, we’re going to locate the Surface System Telemetry driver and completely remove it.
Type Device Manager into Cortana and select it to open. Once it opens, expand out System devices and look for Surface System Telemetry. Right click and select Uninstall.
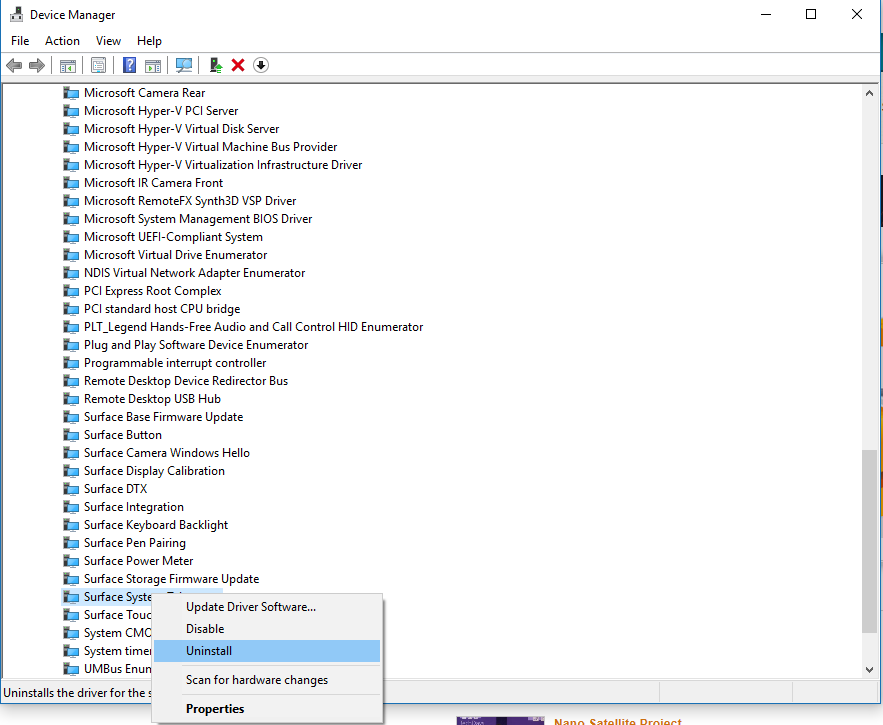
On the prompt, be sure to delete the driver!
Just to be safe, I did NOT reboot after this step.
Next, go out to the internet and grab the latest version of the Surface Book drivers. At the time of this writing, the most recent ones published were from 5/25/2016.
Kick off the install of the drivers from the download and click Next on the first screen.

Agree to the license terms and click Next.
Install to the default location and click Next.
Click Install and after the install, click Finish.
Once the drivers are installed, you will be prompted to reboot. Go ahead and reboot.
The fix should be as simple as that! Like I said, after a week, my Surface Book has been rock solid again. I can safely walk away, stick it in my bag or just leave it for the night and the next time I check it, it wakes up as it should.
I’ve heard that this also fixed the Surface Pro 4 Sleep of Death issues. If you would like to try the same steps, the proper drivers are located here.
Have a question for the members of our Microsoft team? Reach out to them via email at mssales@arrayasolutions.com or by visiting us online at: http://www.arrayasolutions.com/contact-us/

 Following his keynote, Bakker introduced members of Arraya’s technical leadership team for a roundtable on the current state of IT. This panel consisted of Matt Sekol, (Microsoft Practice Manager), Doug Guth (Cisco Practice Manager), Ron Longley (Data Management Practice Manager), Tadd Williams (Microsoft Collaboration Solutions Architect), and Dan Clarke (Senior Solutions Architect). Topics covered during the panel included the right way for businesses to begin their cloud journeys, today’s biggest security threats, balancing end user mobility with security, and exploring the modern data center.
Following his keynote, Bakker introduced members of Arraya’s technical leadership team for a roundtable on the current state of IT. This panel consisted of Matt Sekol, (Microsoft Practice Manager), Doug Guth (Cisco Practice Manager), Ron Longley (Data Management Practice Manager), Tadd Williams (Microsoft Collaboration Solutions Architect), and Dan Clarke (Senior Solutions Architect). Topics covered during the panel included the right way for businesses to begin their cloud journeys, today’s biggest security threats, balancing end user mobility with security, and exploring the modern data center. people more opportunities to catch the classes they were most interested in attending. Among the most popular were sessions on virtual and
people more opportunities to catch the classes they were most interested in attending. Among the most popular were sessions on virtual and  The 2016 Tech Summit capped off with a cocktail reception during which attendees had the chance to enjoy food and drinks, reflect on the day’s sessions, and follow-up with presenters. The
The 2016 Tech Summit capped off with a cocktail reception during which attendees had the chance to enjoy food and drinks, reflect on the day’s sessions, and follow-up with presenters. The knowledge and experience that could help them better serve customers looking to deploy Office 365. The day also served as a preview of what our customers can expect from the upcoming Office 365 Test Drive Roadshow.
knowledge and experience that could help them better serve customers looking to deploy Office 365. The day also served as a preview of what our customers can expect from the upcoming Office 365 Test Drive Roadshow. Wichita, KS. The hospital recently fell victim to a ransomware attack and, in order to regain access to their files, the hospital agreed to pay the ransom. However, the attackers didn’t hold up their end of the bargain. Instead, they only decrypted some of the files and then demanded the hospital pay an additional ransom. Seeing as though patient care hadn’t been affected, the hospital refused, leaving the status of those still-encrypted files in flux.
Wichita, KS. The hospital recently fell victim to a ransomware attack and, in order to regain access to their files, the hospital agreed to pay the ransom. However, the attackers didn’t hold up their end of the bargain. Instead, they only decrypted some of the files and then demanded the hospital pay an additional ransom. Seeing as though patient care hadn’t been affected, the hospital refused, leaving the status of those still-encrypted files in flux. Microsoft and for the businesses who’ve embraced it. In addition to marking Microsoft’s first foray into enterprise voice, E5 contains multiple other features capable of delivering tremendous benefits back towards the business.
Microsoft and for the businesses who’ve embraced it. In addition to marking Microsoft’s first foray into enterprise voice, E5 contains multiple other features capable of delivering tremendous benefits back towards the business.
 However, limitations such as an inability to search cross-server or cross-platform only further complicate the process for those tasked with managing backups.
However, limitations such as an inability to search cross-server or cross-platform only further complicate the process for those tasked with managing backups. this change is increased flexibility. By offering three tiers, each building off the last, VMware has allowed customers to invest in the NSX version that makes the most sense for them, while presenting a clear path for growing their deployments should the need present itself.
this change is increased flexibility. By offering three tiers, each building off the last, VMware has allowed customers to invest in the NSX version that makes the most sense for them, while presenting a clear path for growing their deployments should the need present itself. from the attackers perspective
from the attackers perspective