It’s true whether you’re building a house or securing IT: a tool is only as effective as the person or people behind it. Admittedly we don’t have a ton of expertise in construction. However, IT  security tools are another story.
security tools are another story.
The topic of security has been on our minds quite a bit. So much so that we’ve dedicated a number of blog posts to the topic, including one series on Cisco’s Sourcefire and one on its ISE offering. Our goal in these posts is to lay out the features that set those tools apart and show how they can provide IT with some much-needed peace of mind. Despite our current focus on the tools themselves, we still acknowledge the person(s) using the tool must be a critically important consideration.
In our eyes, there are two main obstacles most organizations run into in this area. For some, it comes down to skill sets. They may not have someone on staff with the necessary experience to manage today’s security solutions and get the most value from them. Getting up to speed on these solutions takes time, all the while an organization could be left vulnerable.
It may also be a question of resource availability. IT has a lot on its plate already and security workloads are likely only going to keep requiring more and more attention. Supporting a growing best-of-breed solution could pull onsite IT away from other, also pressing assignments.
Whatever the case, if IT doesn’t have resources capable of supporting those deployments, then even the most cutting-edge tools may fail to meet expectations. To overcome those obstacles, it helps to have a partner in your corner who not only knows the latest security solutions inside and out, but who also understands your company’s unique needs. This is where Arraya’s Managed Services for Network Security shines.
A hybrid approach to network security
As part of this service, you’ll gain access to our knowledgeable and experienced security experts. Our team is able to shoulder the workload associated with supporting an organization’s security effort, including by providing guidance and insight on how to best prepare for and defend against attacks.
In all of our Managed Services engagements – covering areas such as infrastructure, storage, help desk and more – our team functions as an extension of onsite IT, supplementing and expanding upon the skills of the IT pros already on staff. Whether a task is outside of the expertise of on-site IT or merely consuming too much of its time, our team can handle it.
In the case of Managed Services for Network Security, Arraya will:
- Manage (security) zones, networks and locations
- Inspect, block and alter malicious traffic (using intrusion detection policies)
- Handle early detection, reputation-based blacklisting
- Add or edit access control policies and rules
- Provide 24×7 monitoring and alert response
- Detect, analyze and track files (and protect against malware)
- Generate reports for hosts, users, attacks, malware threats and overall network status
Pairing a Managed Services for Network Security agreement with an industry-leading solution like Cisco’s Sourcefire increases security without increasing the demand placed on today’s already time-strapped IT pros. This “hybrid” approach allows budget and security-conscious organizations to take advantage of an enterprise-grade technology backed by a leading team of support engineers. It’s also scalable, so it’s better positioned to address technology needs, both in the here-and-now and in the future.
Ready to learn more about the latest security offerings from Cisco or a Managed Services for Network Security partnership? Visit us at www.ArrayaSolutions.com. There you’ll find a wealth of resources highlighting the strengths of our Cisco practice as well as our Managed Services team. If you have more questions or are interested in opening up a dialogue with one of our Account Executives, go to www.ArrayaSolutions.com/contact-us.
Be sure to follow Arraya on Twitter, @ArrayaSolutions, for all the latest news, opinions and special offers.

 infrastructure reduces costs, requires less maintenance and allows for the scalability needed to keep up with fluid organizational needs and industry regulations. There’s no doubt the returns can be plentiful, however, the path to the Cloud is rife with potential snares. Organizations who fall victim to those snares can pay the price – both in terms of the budget and the project timeline.
infrastructure reduces costs, requires less maintenance and allows for the scalability needed to keep up with fluid organizational needs and industry regulations. There’s no doubt the returns can be plentiful, however, the path to the Cloud is rife with potential snares. Organizations who fall victim to those snares can pay the price – both in terms of the budget and the project timeline. safely and effectively simply requires IT to take an amended approach to security.
safely and effectively simply requires IT to take an amended approach to security.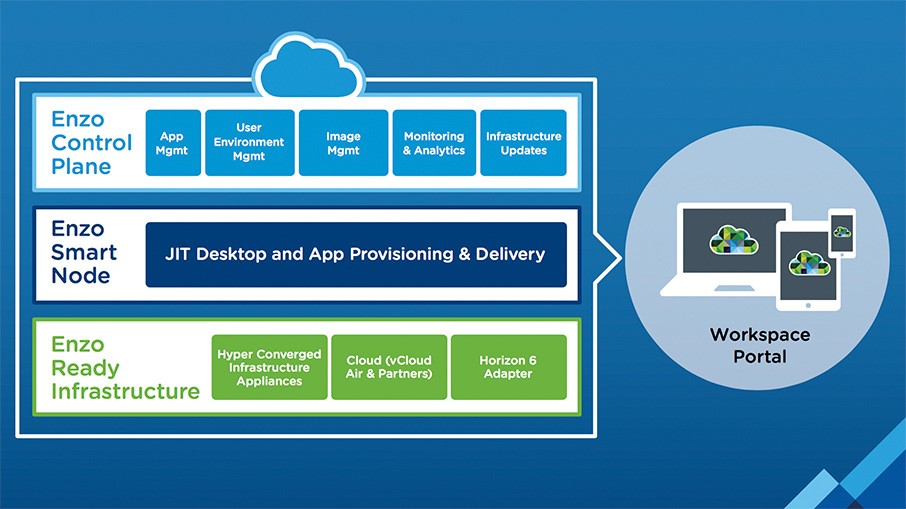
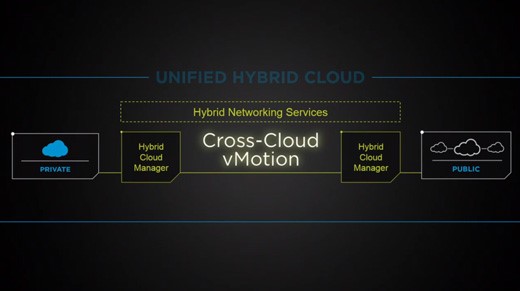
 years. Despite the upsides and the fact that the corporate purse strings have been loosened, there are still obstacles IT will need to overcome before those conversations morph into action items.
years. Despite the upsides and the fact that the corporate purse strings have been loosened, there are still obstacles IT will need to overcome before those conversations morph into action items.

 I’ve been writing a lot on LinkedIn lately
I’ve been writing a lot on LinkedIn lately