Keeping Your Organization Safe with Password Management and DUO 2FA
Most cybersecurity experts will advise employees to keep their personal information off their company-issued devices. In fact, most companies’ acceptable use policies require it. Yet, despite the ample warnings and policies, employees continue to use their work devices for decidedly non-work purposes.
With the growing popularity of remote working, road-warriors, bring your own device (BYOD), etc., it’s time to come to terms with employees using their work devices for personal use as well as professional. From a security management perspective, you must adapt your mindset to help protect your organization’s sensitive data.
Password management applications to the rescue!
Password management applications are not new to the marketplace. However, they have been gaining more attention recently thanks to the high volume of compromised accounts and data breaches. Some key advantages of leveraging a password manager include:
- A different password for every website – The password manager is an encrypted vault for all of your passwords, so you only need to remember one password to get in. This allows for greater password complexity and diversity.
- Simplicity in logging into multiple accounts – You can install browser extensions on all of your devices to autofill your login details.
- Secure sharing – Where permitted, password managers enable you to share passwords securely with co-workers and those you trust.
- Easily update passwords – Password managers allow for easy updating when you have to change your passwords due to expiration or reset.
Some of today’s highest rated password managers include: Keeper, 1Password, LastPass, Dashlane and Bitwarden, just to name a few.
Elevate your enterprise security with Two-Factor Authentication
Two-factor authentication (2FA) strengthens your security by requiring two methods (factors) to verify user identity. The methods used to verify include something that you know, like your username and password, as well as something you have, like a smartphone or even biometrics.
You can tie-in 2FA with password management applications and all of your organization’s important resources to ensure the person logging in is really who they say they are. This extra layer of security is vital to protecting important assets.
One tool Arraya recommends for 2FA is DUO. With DUO, users can carry one device, their smartphone. DUO makes things simple by using something called DUO Push, which utilizes the DUO Mobile authentication app. As a result, users can approve push notifications to verify their identity. Check it out for yourself:
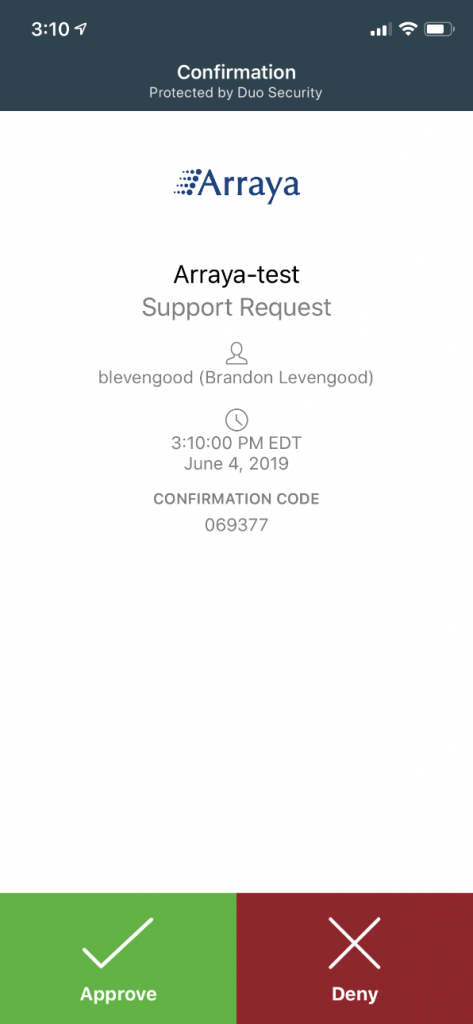
Diving deeper with DUO: Endpoint Visibility
DUO is much more than a basic authenticator. It allows you to use endpoint visibility to track and report on all end user devices from a single dashboard. This lets your organization identify devices that may be at risk. DUO also allows administrators to have granular insight on what devices may be running outdated software so they can get ahead of vulnerabilities that may lead to a data breach.
We talked earlier about the challenges of managing an evolving workforce. DUO can help identify corporate vs. personal devices, supporting organizations in their quest to enable flexibility and data security. By using trusted endpoints, you can utilize device certificates to have greater insight into your BYOD environment. This way, you can easily filter through devices that access your important applications.
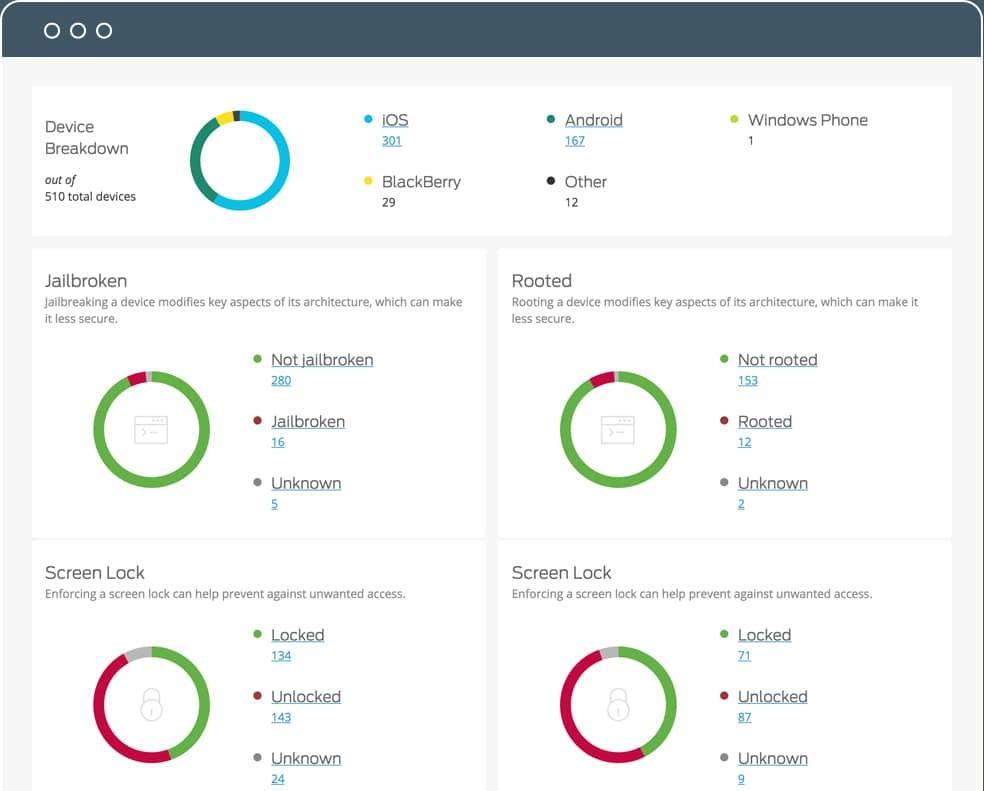
Trusted Access
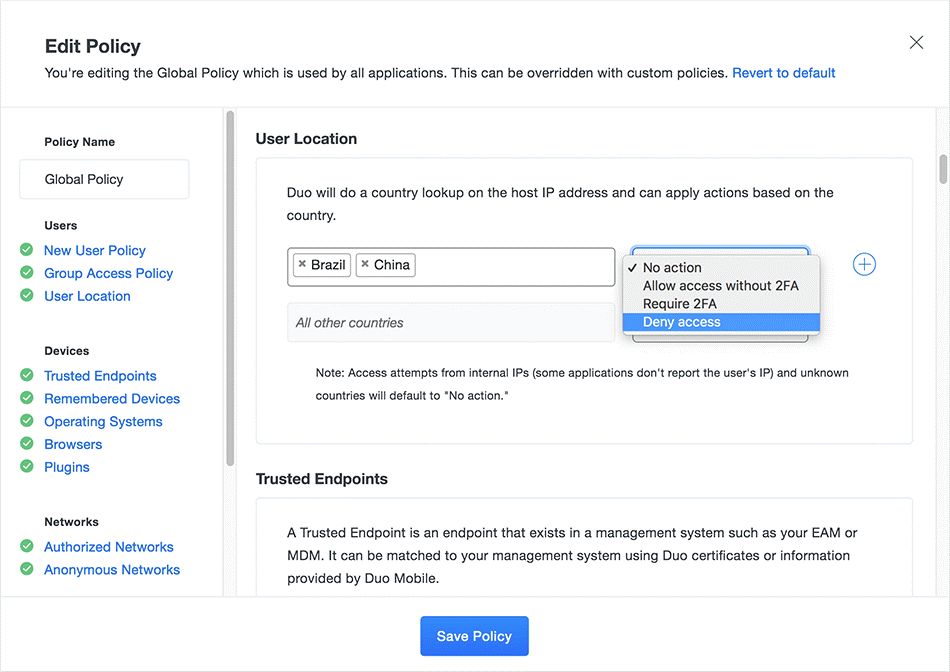
In addition to device visibility, DUO offers policies tailored to the taste of your business needs by using groups, roles, or even responsibilities. Your main priority is simple, protect what is important. By using geolocation, you can easily prevent access from anywhere in the world. You can also control access by IP address or anonymous networks like Tor.
Want to learn more about DUO, 2FA security and building a secure technology environment? Be sure to reach out to our team of cyber security experts now by visiting: https://www.arrayasolutions.com//contact-us/.
