Confidence around a cybersecurity topic is usually a good thing – but not in this case. More than six-out-of-10 (65%) organizations are confident they will suffer a data breach of some kind in the  next year, according to research by Okta. There’s no question that’s the kind of confidence businesses could do without.
next year, according to research by Okta. There’s no question that’s the kind of confidence businesses could do without.
Staying out of hot water requires modern, upgraded cybersecurity solutions. However, even today, when cybersecurity horror stories lurk around every corner, barriers to modernization remain.
Standing between businesses and their cybersecurity goals
Okta’s study featured a list of obstacles, each of which serves to delay upgrades and increase risk. As we reviewed this study, we noticed these obstacles tended to have at least one thing in common: they could be overcome with assistance from a best-of-breed cybersecurity partner.
Here are the top five barriers from the list – and how working with a cybersecurity partner can help:
- Unclear ROI – Roughly 56% of survey respondents said their organization would be hesitant to move forward with a solution unless the ROI was crystal clear.
A cybersecurity partner can help by: performing health checks and assessments to enable a business to better understand its existing cybersecurity environment and how that can be impacted and improved by a proposed upgrade. This gives the business the assurance it needs to move a forward with a plan.
- Access privilege complexity – This dovetails with ROI concerns as it shows businesses’ desire to have a full picture of a change. This is true in terms of ROI and it’s true in terms of access, according to 54% of respondents.
A cybersecurity partner can help by: gathering data on who has access to what within the network. Businesses can use this info to better prepare anyone who may be affected by a move, reducing the anxiety inherent in change.
- Budgetary limits – Budgetary constraints are a familiar wall for IT to bump up against, and 54% of survey participants mentioned it as a key factor stalling upgrades.
A cybersecurity partner can help by: working with a solution vendor to ensure customers have access to flexible buying and leasing options, delivering solutions which are the right fit technically and financially.
- Skills and talent shortages – Just over half (51%) of the businesses included in this study reported not having the skills on staff to manage modern security solutions. If expanding the onsite team isn’t an option, businesses can leverage a cybersecurity partner that also functions as a Managed Services provider.
A cybersecurity/Managed Services partner can help by: providing the customer with the additional hands it needs to manage its growing environment without physically increasing the size of its IT team.
- Lack of scalability – Nearly four-out-of-10 (38%) businesses are concerned they’ll make a substantial investment in a security solution only to promptly outgrow it.
A cybersecurity partner can help by: working with the customer to fully articulate their goals for today, tomorrow, and beyond. With this info, the partner can help design a solution which is capable of growing along with the customer.
Let us help you build the environment you need
Arraya Solutions appreciates the important role cybersecurity plays in organizational success across all industries. We appreciate it, and we’re ready to help businesses reach their ideal cybersecurity environment. We have a long history of working with business to overcome challenges similar to those highlighted above – as well as anything else that comes up during the process of architecting and deploying upgrades.
Ready to talk more about your cybersecurity wish list? Visit www.arrayasolutions.com/contact-us/ to open up a dialogue. We can also be reached through our social media presence: Twitter, LinkedIn, and Facebook. While there, be sure to follow us to keep up with our latest blogs, special events, and industry insights.
Follow along with our National Cybersecurity Awareness Month blog series.
 nature is a unique opportunity to build bridges. It brings technology professionals together in a relaxed setting to network with peers, Arraya team members, and representatives from leading IT vendors. However, there seemed to be added emphasis on that point last week, which was reflected in the speeches given by Arraya CEO Dan Lifshutz as well as by special guest, former Philadelphia Eagles quarterback, Ron Jaworski.
nature is a unique opportunity to build bridges. It brings technology professionals together in a relaxed setting to network with peers, Arraya team members, and representatives from leading IT vendors. However, there seemed to be added emphasis on that point last week, which was reflected in the speeches given by Arraya CEO Dan Lifshutz as well as by special guest, former Philadelphia Eagles quarterback, Ron Jaworski. The day’s other big special guest has also become a fixture in the Philadelphia sports landscape. Chickie’s & Pete’s famous crabfries never fail to draw a crowd regardless of event, and the same was true at Arraya’s Open House. The franchise’s Crabfries Express truck was on hand, dispensing crabfries and chicken fingers to the usual high demand.
The day’s other big special guest has also become a fixture in the Philadelphia sports landscape. Chickie’s & Pete’s famous crabfries never fail to draw a crowd regardless of event, and the same was true at Arraya’s Open House. The franchise’s Crabfries Express truck was on hand, dispensing crabfries and chicken fingers to the usual high demand. the details of how the hack occurred are scarce, clearly Podesta’s entire mailbox was accessed and subsequently dumped. The only detail known is that hillaryclinton.com’s email is hosted at Google (it appears donaldjtrump.com is fronted by Microsoft services).
the details of how the hack occurred are scarce, clearly Podesta’s entire mailbox was accessed and subsequently dumped. The only detail known is that hillaryclinton.com’s email is hosted at Google (it appears donaldjtrump.com is fronted by Microsoft services). hours of 9-5 each day. That is a lot of email. Each one of those 69 billion messages isn’t just an opportunity for workers to connect, it’s also a sizable risk for employers.
hours of 9-5 each day. That is a lot of email. Each one of those 69 billion messages isn’t just an opportunity for workers to connect, it’s also a sizable risk for employers. present, but much less complex than it is today. Most companies had the majority of their IP and other resources locked in an internal network with technologies like NTFS, on-premises applications and team sites in SharePoint.
present, but much less complex than it is today. Most companies had the majority of their IP and other resources locked in an internal network with technologies like NTFS, on-premises applications and team sites in SharePoint.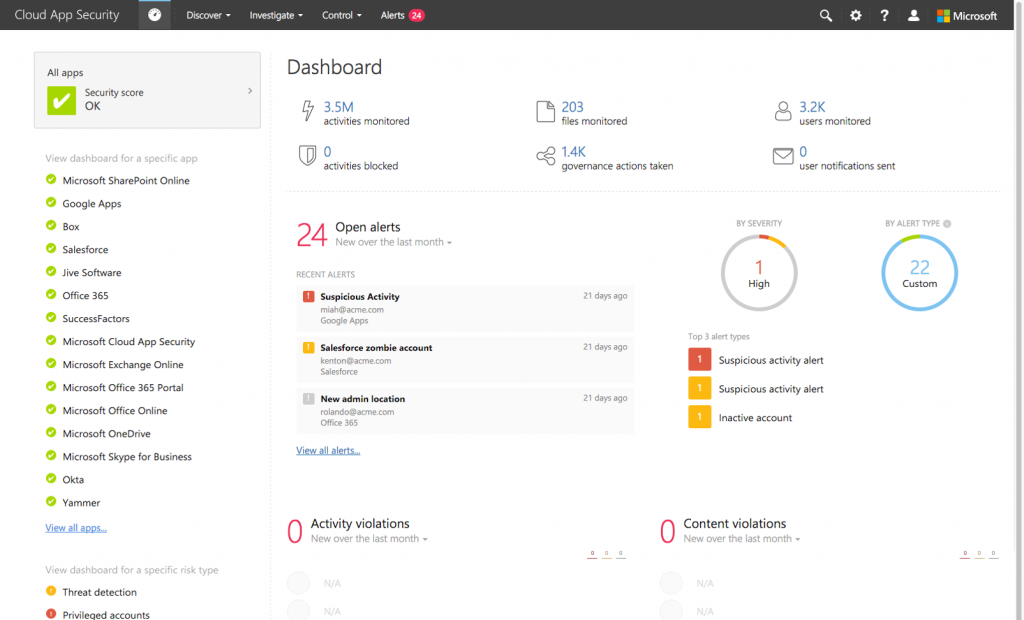
 what could a non-technical knowledge worker possibly do to protect themselves and the company’s data against a hacker?
what could a non-technical knowledge worker possibly do to protect themselves and the company’s data against a hacker? quarter, updating employees on our individual practice areas and the company as a whole. However, I decided to go much further back this time. I went back 17 years, back to when Arraya wasn’t even called Arraya, and compiled all of our biggest milestones into a company highlight reel.
quarter, updating employees on our individual practice areas and the company as a whole. However, I decided to go much further back this time. I went back 17 years, back to when Arraya wasn’t even called Arraya, and compiled all of our biggest milestones into a company highlight reel.

 these engagements. Over the years, we’ve learned plenty about making the process run more smoothly – including the tactics described below.
these engagements. Over the years, we’ve learned plenty about making the process run more smoothly – including the tactics described below.